Now, more than ever, healthcare covered entities such as Health Plans, Physicians and Hospitals must understand where PHI exists, who has access to it and with whom they are sharing it. If your organization can't confidently answer those questions, you may want to consider Sensitive Data Management technology.
G2 Management Group, LLC works with an advanced data technology firm who has developed the first integrated data security solution that discovers, protects and monitors sensitive data at rest and in motion throughout the enterprise without negatively impacting productivity.
In additional to understanding where sensitive data resides and where it goes, healthcare organizations often need to distribute or share data for studies, public health analysis, disease management and other projects. Where PHI needs to be distributed, data obfuscation or de-identification is necessary, especially to comply with privacy standards and good security practice.
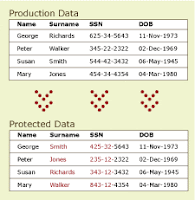
Traditional approaches, such as encryption, often reduce the intrinsic business value of the data. Some Sensitive Data Management tools can mask, encrypt or obfuscate the data depending on the level of security required. Unlike data masking, hashing and scrambling, obfuscation removes the sensitive nature of the data while retaining its intrinsic business value. For example, an obfuscated social security number (SSN) will still look and feel like an SSN to the data consumer. An obfuscated street address will still look like a real mailing address.
Sensitive Data Management tools can help you to achieve compliance with HIPAA privacy and security standards and realize the following benefits:
- Generate desensitized data that looks and acts like real data
- Allow use of desensitized production data for testing
- Maintain referential integrity between multiple source systems over time
- Reduce reliance on endpoint security needs when data is lost via a stolen laptop, USB key, CDs, emailed files, etc.
- Produce consistent, repeatable obfuscation across multiple data extracts and multiple source systems
- Provide ability to access original source system data
- Provide audit trail to demonstrate data validity

